Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns.
Endpoint security systems protect these endpoints on a network or in the cloud from cyber security threats.
Endpoint security has evolved from traditional antivirus software to providing comprehensive protection from sophisticated malware and evolving zero-day threats.
Organizations of all sizes are at risk from nation-states, hacktivists, organized crime, and malicious and accidental insider threats.
Endpoint security is often seen as cybersecurity's frontline and represents one of the first places organizations look to secure their enterprise networks.
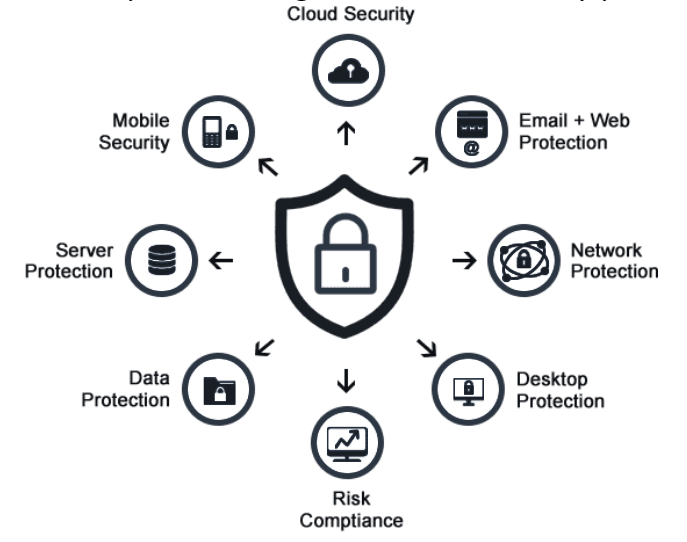
SAVIC offers you a collaborative endpoint management and security platform which can provide real-time endpoint data from a single tool that can re-image remote devices, distribute and patch software, discover and inventory new assets, assess application usage, and monitor and enforce compliance polices across many types of devices using multiple versions of Windows, Mac and Unix/Linux (*nix) operating systems and applications.
The solution is also offered as an independent patch management solution as well as being part of an endpoint management and security platform.
See how companies like yours are succeeding with innovative products, services, and technologies from SAVIC.
Improve outcomes through simplified processes
Leveraging our strategic alliances with technology majors, we
consult with a transparent view on technology, and we help you streamline your IT Infrastructure.
We provide robust software asset management options to customers, right from purchase, management, deployment, maintenance, utilization and modernization of software applications within an organization.
SAVIC is focused on enabling platform-based digital business and technology transformation for
enterprises in the Travel, Retail, Distribution and Software industries.
SAP Activate is an implementation methodology used in SAP S/4HANA and unique combination of 3 core pillars, SAP Guided configuration, SAP Best Practices & Methodology. It is the quickest way till date, to simplify and streamline your business operations with SAP S/4HANA.This methodology enables customers to build smart, run and start faster in their respective landscape.
SAVIC SAP S/4HANA migration templates helps SAP Business Suite customer can move from different start releases to SAP S/4HANA, on-premise edition. For certain start releases, a one-step procedure is available, which includes the installation of the SAP S/4HANA Core and, if necessary, the migration of the database to SAP HANA.
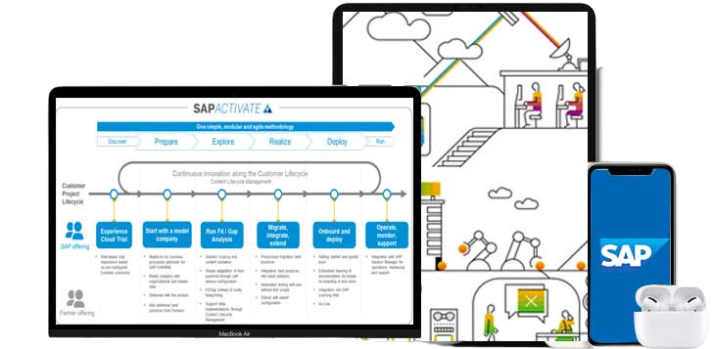
Start seeing everything in your IT environment with
our Implementation services.
Cutover process involves a series of steps need to be planned, executed and monitored in order to make the project golive. It encompass Cutover Strategy, Cutover Plan, The Cutover Date, Agile Monitoring of the cutover activities and Controlling undesired variations.
Keep your systems running at peak performance with SAVIC MAXsupport.
SAVIC technocrat connect to and collaborate with our customers, understand and become part of their value chains, and leverage digital transformation to deliver innovative services and business outcomes instead of selling products.
© 2022 Copyright SAVIC INC.All rights reserved.
Cookie Statement and Privacy Statement
