In times of digital transformation, the success of a business greatly depends on how reliably people, businesses and services are protected against cyber attacks and the loss of valuable data.
SAVIC protects enterprise data, devices and systems. For this purpose, the company relies on the latest technologies, experienced security experts and solutions based on the Zero Trust Model.
The fully integrated Zero Trust Platform supports a broad range of operating systems, endpoint devices, and is offered as an on-premise solution and managed security service.
It combines the elements Data Protection, Endpoint Protection, Endpoint Detection & Response and Identity & Access Management.
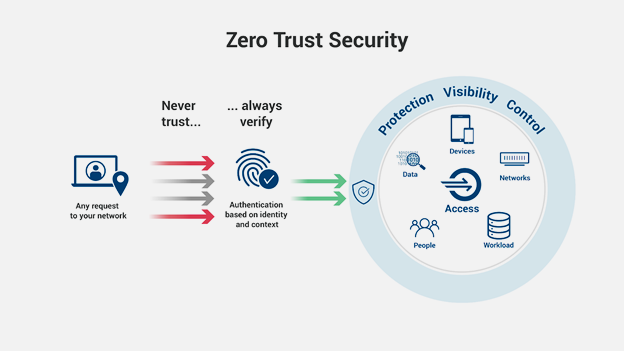
Never Trust, Always Verify
In today's security architectures, Zero Trust means a paradigm shift according to the maxim "Never trust, always verify". One of the cornerstones of protecting our digital lifestyle is preventing sensitive data from being compromised. It is a core of any business strategy that is based on networked digital technologies.
To achieve this, implement a Zero Trust model to ensure that companies assets can be securely accessed and all traffic logged and controlled. Data is reliably protected even within modern business models.
With Zero Trust, you can make cybersecurity the path to business success and differentiation.
SAVIC Zero Trust has the ability to segment, isolate and control the network. Only certain entities with specific requirements can access sensitive network segments or micro-perimeters.
Workload is a high-level term that refers to the entire application stack from the application layer through the hypervisor or self-contained components. As in any other area of zero trust, these connections, applications, and components must be treated as threat vectors and equipped with zero trust controls and technologies. Of particular importance are also the workloads that run in public clouds.
security teams are isolated, secure, and control every device and every computer on the network at all times.
Savic Zero Trust secures and manages data, categorises and develops data classification schemes, and encryptes data both during storage and during transmission are key components of any Zero Trust approach.
This principle describes in the broadest sense the reliable control of the execution of programs, scripts and processes both on the endpoint devices and in the cloud.
SAVIC Zero Trust restricts the user’s access and protects them as they interact with the business. This includes all the technologies needed to authenticate users and continuously monitor and control their access and privileges.
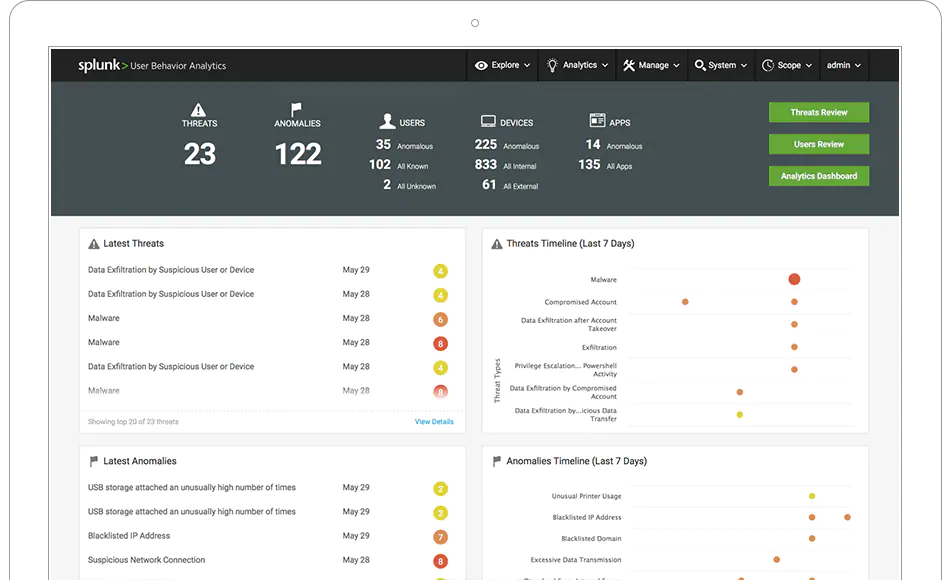
Visibility is the decisive factor in defending valuable assets. It is difficult to protect the invisible or combat a threat that you cannot see or understand. Savic Zero Trust uses tools such as traditional Security Information Management (SIM) systems or advanced security analytics platforms, as well as Security User Behaviour Analytics (SUBA) and other analysis systems enable security professionals to recognise and understand what is happening within the network.
Savic Zero Trust platform uses technologies that enable automation and orchestration. Therefore, it must be possible for leading providers of a Zero Trust platform to be able to integrate with other systems to use complementary security information or pass on useful data. Conversely, companies must be able to automate their operational processes through appropriate orchestration.
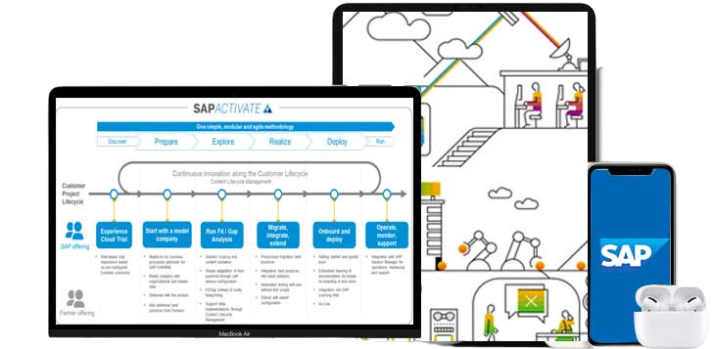
SAP Activate is an implementation methodology used in SAP S/4HANA and unique combination of 3 core pillars, SAP Guided configuration, SAP Best Practices & Methodology. It is the quickest way till date, to simplify and streamline your business operations with SAP S/4HANA.This methodology enables customers to build smart, run and start faster in their respective landscape.
SAVIC SAP S/4HANA migration templates helps SAP Business Suite customer can move from different start releases to SAP S/4HANA, on-premise edition. For certain start releases, a one-step procedure is available, which includes the installation of the SAP S/4HANA Core and, if necessary, the migration of the database to SAP HANA.
| PREPARE | EXPLORE | REALIZE | DEPLOY | RUN |
|---|---|---|---|---|
| 2-weeks | 3-4weeks | 4-6weeks | 2-weeks | 4-weeks |
| Finalize Project Plan | SAVIC Chemical Solution Walk Through | System Readiness – Configure & Develop | Data Conversion & Migration In Production | Hyper Care Support |
| Setup Project Orgnaization & Governance | FIT GAP Analysis Workshop | Unit Testing – Iteration 01 | Mock Cutover | End User Hand Holding |
| Onboarding Project Team On SAVIC Chemical Lab | Delta Business Process Design Document Finalization | System Integration Testing – Iteration 02 | Authorization Setup In Production | System Handover To Customer |
| SAP Sandbox & Development Landscape Setup | R.I.C.E.F.W Finalization | User Acceptance Testing – Iteration 03 | End User Training Deployment | Knowledge Transfer To AMS Team |
| Business Process Master List (BMPL) Finaliza on | Authorization Approach Finalization | Data Conversion & Migration In Quality (25% Of Total Volume) | Setup Hyper Care Support Organization | |
| Business Process Master List (BMPL) Finaliza on | Data Migration Approach Finalization | Training Preparation & Depolyment | Final Validation and Go-live | |
| SAP KDS (key Data Structure) Finaliza on | Core Team Training Approach Finalization | Cutover Strategy Finalization | ||
| Test Strategy Finalization | Production environment Setup | |||
| Quality Environment Setup | SAVIC Quality Team Audit |
Start seeing everything in your IT environment with
our Implementation services.
Cutover process involves a series of steps need to be planned, executed and monitored in order to make the project golive. It encompass Cutover Strategy, Cutover Plan, The Cutover Date, Agile Monitoring of the cutover activities and Controlling undesired variations.
Keep your systems running at peak performance with SAVIC MAXsupport.
© 2022 Copyright SAVIC INC.All rights reserved.
Cookie Statement and Privacy Statement
